For a long time, there was a clear red line for cybercriminals and state-sponsored adversaries: hospitals and healthcare infrastructure were off limits. In many minds, this long-gone honeymoon period still persists. The belief that no one would want to harm hospitals and clinics remains widespread.
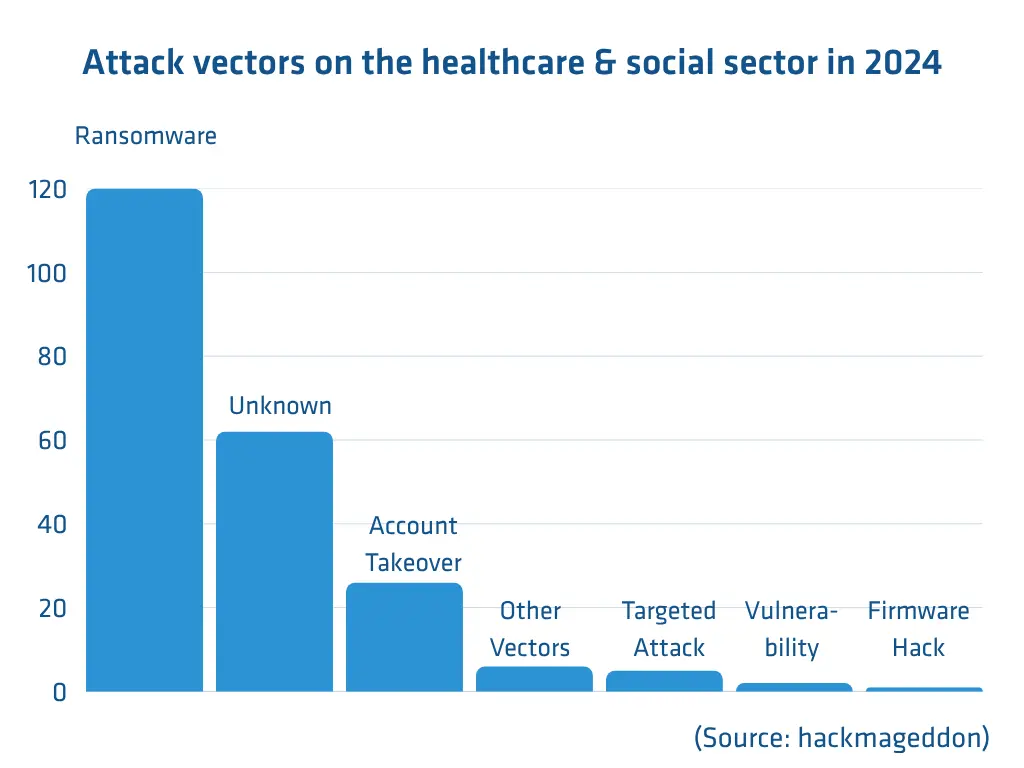
Yet for several years now, healthcare has been one of the critical sectors most affected by cyberattacks. Of the 289 incidents in the healthcare sector reported to European authorities in 2024, 49 were cyberattacks1. This puts healthcare in third place after the energy (84) and transportation (65) sectors.
Globally, there have been nearly 1,600 reports of cyberattacks on healthcare facilities in the past five years.2
At the same time, the interconnection of operational technology (i.e. medical devices, building automation systems) is growing in the healthcare sector. Electronic patient records, robot-assisted telesurgery, centrally controlled building automation for HVAC (heat, vacuum, air conditioning), and the supply of a wide variety of gases are leading to the increased digitalization of clinical processes.
What are the blind spots in the cybersecurity of medical devices and systems?
The somewhat simplified answer is that operational technology often constitutes a single blind spot. Certainly, HVAC systems, medical devices, and hundreds of display panels are maintained by maintenance technicians as well as equipment vendors. However, they are not concerned with cybersecurity, but only with basic operational functionality.
In most cases, the IT department is not even aware of of the operational technology as part of their security strategy, simply because it was not really necessary in the past – or because the systems were too specialized (and air-gapped).
In addition, there is often a false sense of security. Hospital IT is typically protected by firewalls. In theory, this also secures the operational technology. However, traditional firewalls are blind to certain attack vectors, such as:
- Zero-day vulnerabilities,
- attacks via stolen access data (stolen credentials), which are now the most common initial attack vector,
- insider threats,
- attacks via medical device firmware (supply chain compromise).
In a nutshell: Once adversaries are inside the network, no firewall will help.
The fact that medical devices and operating technology are usually (or can be) operated air-gapped and are often only connected to the internet for maintenance purposes offers no protection either. Not only are these short maintenance windows sufficient for adversaries to compromise systems, but the increasing level of networking is also making this supposedly secure state a thing of the past. In hospitals, IT and operating technology, and thus also operating technology and the internet, are becoming increasingly interconnected.
An industrial network intrusion detection system for hospital OT?
From the perspective of operating systems and the communication protocols used, medical devices are very similar to IT. However, in terms of communication structure and patterns as well as core requirements, they are much more similar to industrial networks (i.e OT). Commands and communication are deterministic, uniform, and repetitive. Data protection is important, but always takes a back seat to availability and reliability.
For this reason, medical devices share another characteristic with industrial components and networks: they do not inherently include cybersecurity mechanisms, nor were they hardened during development. Outdated operating systems, confirmed vulnerabilities, weak authentication, or a lack of mechanisms to block malicious communication are not uncommon. Truth is that this is not going to change anytime soon.
Network monitoring protects medical equipment
This means that those responsible in hospitals and clinics are faced with the challenge of managing the residual risk that cannot be eliminated, with a focus on availability.
This is not possible on the devices themselves, as they are not designed for this purpose. Consistent network segmentation helps to cluster risk zones. However, only a network-based intrusion detection system (NIDS) enables unwanted (i.e., malicious) communication processes within networks to be detected at an early stage.
A NIDS such as Rhebo Industrial Protector reads all communications between devices in the network. Since it recognizes and understands both the prevailing IT protocols and industrial protocols, it provides a comprehensive view of operational technology cybersecurity. Unusual, new, or changed communication patterns are detected in real time and can be immediately assessed for risk.
In addition, known vulnerabilities and misconfigurations (e.g., in network segmentation or in relation to automated factory settings of device firmware) are detected and can be subsequently remedied.
Those responsible for operational technology as well as the IT department can thus make quick, informed, and coordinated decisions to ensure both data protection and system availability.
